IDC MarketScape: European Managed Security Services 2022 Vendor Assessment
←
→
Page content transcription
If your browser does not render page correctly, please read the page content below
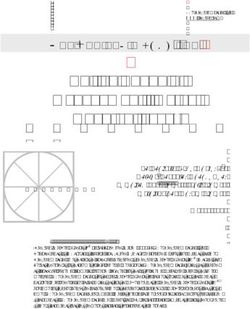
IDC MarketScape IDC MarketScape: European Managed Security Services 2022 Vendor Assessment Claudio Stahnke Joel Stradling THIS IDC MARKETSCAPE EXCERPT FEATURES ORANGE IDC MARKETSCAPE FIGURE FIGURE 1 European Managed Security Services Source: IDC, 2022 Please see the Appendix for detailed methodology, market definition, and scoring criteria. January 2022, IDC #EUR146178820e
IN THIS EXCEPRT The content for this excerpt was taken directly from IDC MarketScape: European Managed Security Services 2022 Vendor Assessment (Doc # EUR146178820). All or parts of the following sections are included in this excerpt: IDC Opinion, IDC MarketScape Vendor Inclusion Criteria, Essential Guidance, Vendor Summary Profile, Appendix and Learn More. Also included is Figure 1. IDC OPINION The managed security services (MSS) segment is a growing market in Europe as businesses of all sizes seek to manage and control their security and data privacy needs amidst seismic changes driven by the pandemic, growing volumes and sophistication of cyberattacks, and an acute talent shortage. The MSS market has expanded within Europe, and several players have been successful in growing their market shares. Several factors drive growth in pan-European MSS. In addition to the pandemic driving a spike in employee remote access, most IT departments struggle to address growing security complexity as the organizations they serve proceed with public and hybrid cloud adoption and other digital transformation initiatives. Companies are looking to zero-trust security principles to help defend against threats in line with the assumption that "we have been breached" to prevent further damage and lateral movement of cybercriminals within the IT infrastructure perimeter, be that virtual or physical. However, adopting zero trust is a steady journey rather than an overnight job, and many businesses seek assistance with advisory as well as planning and implementation from their MSS providers (MSSPs). Currently, there is strong demand for innovative security capabilities including extended detection and response (XDR), and more visualization in enriched monitoring tools enabled by the application of AI/ML to data analytics. As with zero trust, developing an XDR platform might be challenging for organizations, and opportunities exist for MSSPs to offer some form of managed XDR, which will include help setting up a platform and integrated with current security systems. In parallel, we see ongoing evolution of software-defined network (SDN) services, threat intelligence and threat hunting, and incident response retainers, with all types of add-ons or value-added capabilities designed to boost cyber-resilience, lower risk, and promote trustworthiness. Trust encompasses several factors beyond purely technical security to areas such as sustainability, diversity, and brand. As such, the CISO's role — and the overall function of IT security — is also evolving toward business outcome-oriented themes, and the MSSPs within this report offer varying approaches to help support customers with these role and organizational adjustments. European organizations are bound by complex pan-regional and local regulatory rules, such as GDPR and NIS, as well as other country- and industry-specific cyber rules. The European Union enforces the rules laid out within Payment Services Directive Two (PSD 2), while Brexit has resulted in U.K.-specific variants of GDPR and NIS. European businesses need to legally abide by all security and privacy implications of the regulations. MSS are thus an attractive proposition for pan-European businesses to help with their targets for regional and global expansion, boosting or enabling efforts to take advantage of growth opportunities in a digital economy. Europe has very distinct cultures and languages, and this results in small, regional MSSPs that may have localized pockets of strength. Feet on the ground and local languages matter, and ©2022 IDC #EUR146178820e 2
security operations center (SOC) and datacenter presence are very important to European
businesses. Meanwhile, concerns regarding the security of cloud-based user data must be
navigated to ensure compliance with local (i.e., country-level) and regional regulations, particularly
GDPR and its equivalents.
The regional intricacies of the pan-European market, such as a significant number of former public
switched telephone network (PSTN) incumbents, has given rise to the presence of multiple
provider categories in the market as follows:
Security technologists
Telcos
Systems integrators (SIs)
Audit and consulting firms
Defense contractors
Regional specialists
This IDC MarketScape study compares 14 organizations that offer MSS in Europe. Due to the
inclusion criteria of this study, majority of the region's most significant MSSPs were included in this
assessment.
MSSPs can better differentiate from other players in the market by possessing abilities to support
European data sovereignty and through solid, feet-on-the-ground presence for sales and
marketing support. Successful MSSPs will also exhibit thorough capabilities to deliver sales and
technical support in multiple languages plus in-region SOC infrastructure and global MSS delivery
models (either 24 x 7 or follow-the-sun or FTS, or sometimes both). Typically, an MSSP would also
need to back up these pan-European capabilities with a range of complementary capabilities such
as forensics, breach response, and incident response (see the Appendix for details).
The MSSPs featured in this study operate global delivery models but can also provide more
specific local or regional support models, albeit on a custom basis. The European Union's General
Data Protection Regulation (GDPR) relates to the processing of personal data that may, but does
not always, feature as an element of security operations data capture and transfer. Importantly, in
such cases, a legal mechanism is required for the transfer of personal data across international
borders in cases in which data is being transferred beyond the EU.
An important feature of MSS propositions for the European market is the ability to handle diverse
customer expectations around security operations data residency and transfer.
European MSS IDC MarketScape Drivers
Disruption from many directions: cyberattack, technology start-up disruptors,
disinformation, extreme weather, supply chain shortages, inflation, and political turmoil
The evolution of analytics and intelligence applied to advanced security solutions and
executed by artificial intelligence (AI)/machine learning (ML)
Growing take-up of XDR, including various flavors of managed XDR
Compliance and GDPR, including data sovereignty
Trust and digital resilience
Risk measurement, scoring, and remediation
©2022 IDC #EUR146178820e 3European Specifics
European Businesses Require Privacy and Data Security Compliance
On the topic of regulatory requirements surrounding data transfer, the major consideration is the
European Union's GDPR, which relates to the processing of personal data. A legal mechanism is
required for the transfer of personal data across international borders including beyond the EU.
The definition of what constitutes personal data may require special attention. For example, within
GDPR, the EU includes IP addresses and business email addresses that contain an individual's
first and/or family surname within the classification of "Personal Identifiable Information" and are
therefore subject to privacy protection regulations. This is not necessarily the case for MAC and
over-the-top (OTT) provider assigned email addresses that may not reveal personal names (in
other words, the email address contains a numerical string only).
Geographical and Languages
This pertains to having multiple points of presence with local representation to tackle diverse
European needs. For example, Italy has a very substantial SME base that delivers innovative
products across Europe. Similarly, the German economy has a large industrial and manufacturing
sector based on small, family-run businesses, in addition to its significant automotive industry.
It's easy to forget that English is not spoken widely beyond Northern and Western European
countries, and German or Russian have become more popular the further east one travels.
Therefore, an understanding of local idiosyncrasies and preferences is important, as well as the
ability to converse in local languages.
Therefore, the question of data residency and data handling has two elements for Western
European MSS buyers and MSSPs alike. First, GDPR requires organizations to retain personal
data within the EU, or only to work with MSSPs able to support international data transfer models
through enabling legal mechanisms. Second, regardless of regulatory requirements, some
organizations will simply refuse to countenance the transfer of data outside the EU — or even
outside their home countries — due to their perception of robust operating models and security and
privacy practices.
Germany, Italy, and Finland are particularly hostile to data transfers, but there are plenty of
individual companies in other countries that exhibit similar antipathy.
MSS is a highly competitive marketplace, yet security is a largely horizontal market, which makes it
difficult for vendors to generate true differentiation. Therefore, European MSS customers must
consider three key themes when assessing potential MSSPs:
Does the vendor possess the right infrastructure to meet my security operations data
handling requirements?
Does the vendor possess the breadth of portfolio needed to meet my future needs, not just
my needs right now?
Does the vendor understand my business needs, and can it provide MSS in a way that
supports my goals?
IDC MARKETSCAPE VENDOR INCLUSION CRITERIA
IDC collected and analyzed data on 14 MSSPs in the 2022 IDC MarketScape European Managed
Security Services Market Assessment. While the market arena for MSS is broad and there are
many suppliers that offer these services, IDC narrowed the field of participants for this study based
on the following criteria:
©2022 IDC #EUR146178820e 4 Service capability across the MSS life cycle. Each service provider was required to
possess full-service MSS delivery capabilities (see Appendix for an explanation of MSS).
Scale. Each service provider was required to command a leading level of scale within the
European MSS marketplace. As a proxy for scale, IDC decided to measure this element
based on revenue, whereby each provider was required to have achieved total MSS
revenue for Europe of at least $60 million in 2020.
Geographic presence. Each vendor was required to have MSS delivery capability for the
European region and possess at least one multitenant SOC in Europe. This SOC presence
must form part of either a 24 x 7 or FTS support model (see the Appendix section for an
explanation of MSS).
ADVICE FOR TECHNOLOGY BUYERS
All the MSSPs have a similar list of technology partners such as Check Point, Palo Alto
Networks, and Fortinet. Differentiation is a very fine line — buyers can check the tech
partner ecosystem that the MSSP offers. Providers may have their own IP to create
differentiation, but buyers need to assess the benefits of this against any concern of lock-
in. Some MSSPs will have fewer security partners and go very deeply into the products
that the partner provides, while others might have many more partnerships, but these
relations might be shallower (for example, they do not include joint R&D activities or
collaborative go-to-market efforts). There is no hard definition on which is better; it is just
something that customers ought to consider.
Look for a provider that will invest in understanding your existing IT security footprint as
well as the evolution and road map to a more modern security capability. MSSPs should
be offering flexibility terms and contract choice to meet individual needs.
Proven success in offering security to businesses in the same vertical.
Scale — an SME also needs a global MSS. Supply chain attacks mean that even small
businesses are under attack, and MSSPs should be offering services that cater to this
particular segment.
The three points of advice provided at the end of the IDC Opinion section can help MSS buyers to
generate a shortlist based on the critical criteria required for support and/or rule out potential
vendors that do not meet these criteria. However, further analysis is likely required to establish the
suitability of the remaining shortlisted providers. In the following section, IDC highlights 11
considerations that can help buyers distinguish between prospective MSSPs.
Enterprises Seek Assistance With Detecting Zero-Day Attacks as Part of
MDR
Figure 2 shows the responses to the question: "Where do you require the most assistance with
your MDR services?"
©2022 IDC #EUR146178820e 5FIGURE 2
Enterprise MDR Adoption Drivers
Q. Where do you require the most assistance with your MDR services?
Source IDC European Security and Privacy Annual Survey, July 2021
Adding managed detection and response (MDR) to a managed security services contract.
One of the qualifying criteria for vendors in this study was the possession of full life-cycle
MSS services, or the ability to offer advanced services (see the Terminology section in the
Appendix), such as MDR and threat hunting with AI/ML-enabled data analytics for more
rapid and automated detection and response. Buyers are advised to consider which of
these advanced capabilities are significant or even strategic to their needs.
Risk quantification and remediation of known risks. Businesses need to understand where
their security vulnerabilities lie and have the risks associated scored. Afterward, ongoing
programs should be in place to address those risks and reduce the level of exposure.
Automation and orchestration. One of the main drivers for MSS adoption in general is the
lack of availability for security resources (both personnel and otherwise) with which to
conduct security operations. While a larger pool of resources is a reason to engage
MSSPs, it is also worth considering how they can augment both your own in-house
resources and their third-party resources through technology. Here, the ability to automate
security tasks and orchestrate security processes can represent a source of added value
for MSS customers and a method to accelerate response to threats.
©2022 IDC #EUR146178820e 6 Threat intelligence (TI). MSSPs can achieve market differentiation via the scale, breadth,
and depth of their threat intelligence. Differentiators may include the geographic reach of
threat intelligence collection, the source of its collection (e.g., via network infrastructure,
SOC locations, threat research teams), the breadth of third-party partners, the portal
through which it is accessed, and the manner of classification. Some MSSPs offer threat
intelligence as a service, perhaps as a component within a standard MSS portal through
which threat intelligence can be delivered against agreed parameters. Buyers should
consider not just the scale and variety of TI that is on offer, but also how MSSPs can help
them consume it.
Cloud security. MSSPs' approach to the cloud is an important consideration. MSSPs must
be able demonstrate that they can monitor and protect their customers' activities across
on-premises, private cloud, public cloud, and hybrid environments. Smaller enterprises
seeking MSS support are advised to seek MSSPs that can address their needs through
cloud delivery, offering MSS with flexible pricing options.
MSS portals. User portals should offer ease of use, visibility, and management
convenience for the security and privacy tools in place. Customers are advised to ask
MSSPs about how they are incorporating Big Data analytics and threat intelligence into
their portals. Customers may ask whether they can manage parts of their security estates
via mobile apps.
Innovation and R&D. While many MSSPs can meet specific technical requirements, how is
the vendor helping to drive the market forward? Not all vendors have an equal commitment
to the incorporation of R&D and innovation into their future road maps. Automation and
orchestration are increasingly important MSS considerations, and with a large proportion
of security needs still tied to the network, innovation in network functionality is therefore a
key consideration. Enterprises are advised to challenge MSSPs on how they propose to
harness the potential of emerging technologies, whether directly through their MSS
portfolios, through complementary capabilities, or even as part of broader engagements.
Broader portfolios. Buyers are advised to consider how vendors can contribute to business
strategies through their ability to combine MSS and complementary security services with
their broader IT and network services. This leads to further considerations, such as
whether it is simpler from a supplier management perspective to engage an existing
provider on a broader basis, or whether it is more beneficial to engage a third party to
provide an independent security perspective.
Relationship management. IDC advises that the relationship between an MSSP and its
customers ought to be a partnership rather than being transactional in nature. While
relationship features such as an account manager, account reviews, and road map
reviews are standard practice, the frequency of engagement varies between providers.
MSS buyers must consider how often they are likely to need guidance from providers,
insight into their plans, and opportunities to review their relationships.
Packaging and preconfiguration. While fully customizable MSS might be suitable for large
enterprises, MSSPs must also be able to demonstrate packaged and preconfigured
solutions. Customers in this market segment are advised to challenge MSSPs to
demonstrate that they can offer solutions that are not only "good enough" to meet their
security needs, but are also not overly taxing either operationally or financially, making
them realistic propositions for use by small and midsize organizations for which security is
likely to be wrapped up within the role of IT, rather than possessing dedicated teams.
©2022 IDC #EUR146178820e 7 Routes to market. Some MSSPs appreciate the role of the channel in extending their
reach, either to engage markets where they lack a direct presence or support the needs of
smaller clients that may prefer to deal with a small provider. A special mention must be
made for the MSS businesses of telco operators, which are strongly represented in this
study. Despite a large enterprise focus in common with their peers in communities such as
SIs and audit/consulting firms, they also tend to have a strong track record in engaging
small customers directly due to their heritage in network services. For these organizations,
the breadth of their channel programs may be less significant (but still not irrelevant) for
their ability to reach all segments of the market.
Delivery Models, Data Residency, and Data Transfer
The 11 attributes highlighted previously offer avenues for MSSPs to show differentiation and
enable buyers to hone their shortlists. However, IDC views that the key consideration driving buyer
behavior will be delivery models, as well as the approaches to security operations data residency
and transfer that these delivery models enable.
Prospective MSS buyers need to consider which of these two paradigms will be most suited to
their needs:
A global delivery model capable of providing MSS support for European organizations both
at home and across their international operations. This will likely require a follow-the-sun
support model, involving handover of support shifts (and security operations data) between
various regions to provide continuous support. This model is likely to maximize the
benefits of cost and scale that the largest providers can offer.
A locally oriented delivery model that provides continuous MSS support for European
organizations without having to resort to extra-regional resources and locations. This
approach avoids the need to hand over shifts between regions and the need to transfer
security options beyond the region (or even the country) of support. However, this will
likely require customers to work with either local specialists that lack insight into the global
threat landscape or global providers on a custom basis to deliver these capabilities from
their local resources (albeit this may come at a cost).
Some organizations, particularly those based in Europe, have a strong consideration for the
localization of their security operations data. However, it is worth considering that the regulatory
requirements may be less stringent than is often perceived. In many cases, it is merely a question
of comfort for the decision maker or organizational culture that dictates whether an in-region or in-
country model for MSS delivery is required.
The most mature MSSPs will be able to accommodate the full range of considerations, assembling
a delivery model and security operations data handling approach that suits the needs of the client.
However, buyers must acknowledge that these decisions ought to be made based on managing
organizational risk. It may be that a fully in-region, 24 x 7 support model is required, but given the
cost implications, this decision must be driven by an explicit business risk requirement rather
satisfying a perceived issue that may or may not represent a true risk for the organization.
MSS buyers may challenge potential MSSPs about the mechanisms these vendors have
developed to achieve GDPR, such as adequacy, standard model clauses, and binding corporate
rules.
©2022 IDC #EUR146178820e 8VENDOR SUMMARY PROFILES This section briefly explains IDC's key observations resulting in a vendor's position in the IDC MarketScape. While every vendor is evaluated against each of the criteria outlined in the Appendix, the description here provides a summary of each vendor's strengths and opportunities. Orange IDC positioned Orange in the Leaders category in this IDC MarketScape for Managed Security Services in Europe. Orange Cyberdefense, part of the Orange Group, is a global provider of managed services and managed threat detection and response services. Its global operation was created via the acquisitions of SecureLink UK and SecureData Europe. The SecureLink acquisition boosted Orange Cyberdefense's capabilities in China, Germany, the Netherlands, Norway, Denmark, and Sweden as well as added capabilities in Belgium. The SecureData acquisition provided access to global portfolios and direct presences in the U.K. and South Africa. Orange Cyberdefense offers an Emergency Cybersecurity Incident Response service to help its customers respond to cyberthreats quickly and effectively. The offering is backed by a specialist Computer Security Incident Response Team (CSIRT). Not all European MSSPs have this capability since they outsource incident response. Orange Cyberdefense can differentiate its proposition by leveraging expertise and understanding of network and security architectures. It can combine these with the monitoring of end-user behavior, integrations with multiple security vendors, and knowledge and experience in how cybercriminals think and behave as they seek to exploit vulnerabilities. Orange Cyberdefense has evolved its MSS services to include an advanced XDR product. Its XDR supports visibility of security data from endpoints and monitors network traffic and selected log data. Orange Cyberdefense can implement managed threat detection on behalf of its clients, and then offer ongoing supervision and maintenance. Orange Cyberdefense builds go-to-market messaging around how it can help customers through the application of an intelligence-led approach. In cybersecurity, threats emerge because of a complex system of interacting factors. Orange Cyberdefense reports a strong increase in ransomware attacks. Orange Cyberdefense is in a solid position to analyze these factors. It can protect its customers by leveraging the intelligence from its operations as well as via external intelligence feeds, collaboration with law enforcement, visibility into network traffic as an operator, in-house R&D, and more than other 500 sources. Backing up the intelligence feed is a staff resource comprising 2,500 security experts and a pan- European SOC footprint comprising nine SOCs with facilities in France (x2), Belgium, the U.K., the Netherlands, Sweden, Norway, Germany, and Poland. Orange Cyberdefense reports 8,000 customers worldwide and achieved 9% growth to its year-on- year revenue. In its recent Q3 earning repots, Orange Cyberdefense claims 14% growth for the nine months year-to-date (January to September 2021) compared with the equivalent period in 2020. ©2022 IDC #EUR146178820e 9
Orange Cyberdefense can deliver a blend of products and services to span network connectivity based on software-defined secure access and zero-trust network architectural principles for secure cloud access. Orange Business Services can support pan-European SD-WAN services leveraging considerable on-net coverage and third-party network peering relations with Orange Cyberdefense, layering on top of the network several value-added security features and services such as security monitoring, incident response, and identity and access management. Orange Cyberdefense offers flexible commercial models. It can, for example, offer an opex-based, fully managed service that it will control, or if the client prefers, it can offer the technology platform that the client owns with Orange Cyberdefense, providing its services on top of the platform. In terms of user portal and MSS customer experience, customers can leverage the new native XDR service and source the Orange Cyberdefense Fusion center to access and manage their security portfolios. Customers are able to leverage the Orange Cyberdefense user portal or "Customer Hub," which is one of the front-end bricks within the MSSP's Fusion Center. The Fusion Center automates processes to drive synergies across CyberSOC, SOC, and CERT services as well as streamlines analytics and intelligence across services. The Orange Cyberdefense Fusion Center supports multiple components including inputs for cyber-risk management and detection of fraudulent activities. It supports native XDR and an integrated XDR service that includes endpoint protection, network analysis, identity access management, cloud analytics, and analytics and monitoring for applications. The Fusion platform also processes inputs from IoT implementations and business systems to help prevent risk and exposure. In terms of services that sit of the Fusion platform, Orange Cyberdefense leverages Fusion to offer incident response retainers, portal alerting and reporting, and active response services. For the cloud, the Fusion platforms provides monitoring, detecting, and responding to threats. Strengths Orange Cyberdefense has excellent credentials for interpreting threats with context on behalf of its customers, and thus advise them on where to invest to best protect against cyber-risk. The company's threat research and Cybercrime Monitoring teams are differentiators in a crowded market. Orange Cyberdefense can provide this contextual insight both within the corporate perimeter and in the dark web. Orange Cyberdefense's Threat Intelligence product is backed by a data lake fed by more than 500 external sources such as governments, honeypots, partners, and internal sources such as its network backbone, CyberSOCs, CSIRT, and vulnerabilities identified by the CERT team, or pen- testing team. With considerable scale and Orange Group synergies with major fixed and mobile networks across the world, Orange Cyberdefense reports that its CyberSOCs capture 50 billion logs per day. Orange Cyberdefense's sister company Orange Business Services provides tremendous upsell/cross-sell opportunities and is a recognized global advisor to major enterprises on their secure digital transformation trajectories including cloud adoption. It also has local operations and proximity blended with global reach and operations. Orange Cyberdefense can offer a compelling message around full life-cycle services to secure transformation and new cloud adoption programs. Challenges Orange Cyberdefense tends to lean on multiple technology partnerships for building its MSS range rather than establishing its own IP. ©2022 IDC #EUR146178820e 10
Consider Orange When Converged network, cloud, and security are major aspects of the RFP for an MSSP. Orange Cyberdefense is well positioned to offer solutions that span network connectivity based on software-defined secure access and zero-trust network architectural principles for secure cloud access. Orange Cyberdefense has a dominant local market presence and infrastructure within domestic France. MSSP competitors will not be able to match the company's pan-European scale and presence. When shopping for a portal and user experience that blends XDR service capabilities (customer may ask to evaluate the Fusion platform). APPENDIX Reading an IDC MarketScape Graph For the purposes of this analysis, IDC divided potential key measures for success into two primary categories: capabilities and strategies. Positioning on the y-axis reflects the vendor's current capabilities and menu of services and how well aligned the vendor is to customer needs. The capabilities category focuses on the capabilities of the company and product today, here and now. Under this category, IDC analysts will look at how well a vendor is building/delivering capabilities that enable it to execute its chosen strategy in the market. Positioning on the x-axis or strategies axis indicates how well the vendor's future strategy aligns with what customers will require in three to five years. The strategies category focuses on high- level decisions and underlying assumptions about offerings, customer segments, and business and go-to-market plans for the next three to five years. The size of the individual vendor markers in the IDC MarketScape represent the market share of each individual vendor within the specific market segment being assessed. IDC MarketScape Methodology IDC MarketScape criteria selection, weightings, and vendor scores represent well-researched IDC judgment about the market and specific vendors. IDC analysts tailor the range of standard characteristics by which vendors are measured through structured discussions, surveys, and interviews with market leaders, participants, and end users. Market weightings are based on user interviews, buyer surveys, and the input of IDC experts in each market. IDC analysts base individual vendor scores, and ultimately vendor positions on the IDC MarketScape, on detailed surveys and interviews with the vendors, publicly available information, and end-user experiences in an effort to provide an accurate and consistent assessment of each vendor's characteristics, behavior and capability. Market Definition The security landscape is complex and challenging — an understatement given the number of moving parts that are involved in defending an enterprise from cyberattacks. IDC recommends that companies adopt a holistic, enterprisewide security posture that is both proactive and predictive. It is a daunting effort, however, to achieve this goal. It requires enterprises to sustain the necessary volume of threat intelligence and advanced analytics capabilities, along with the skills to interpret and act on findings. In-house 24 x 7 security solutions are expensive, and security talent is scarce. ©2022 IDC #EUR146178820e 11
Thus, organizations face a debate of "build versus buy," and many are turning to MSSPs. A
security services provider can allow organizations to meet several objectives:
Transfer the cost of ownership, thereby reducing capex and transferring the budget to
opex
Create a predictable expense with a regular cadence in the budget cycle
Enable a dedicated application of technology, processes, and people to the rapidly
changing threat landscape
Implement best practices that are evolving with a rapidly changing threat landscape
Benefit from "strength in numbers" from an intelligence perspective
The rise in frequency and complexity of attacks and the need for increasingly sophisticated security
solutions have led to a new, second-generation echelon of MSS that IDC calls MSS 2.0. An MSSP
that can provide a 2.0 proposition sits further "up the stack" of strategic value and influence than
MSSPs that are offering only MSS 1.0 services.
MSS 1.0 services include the following:
Log monitoring
Basic managed and monitored services (firewalls, intrusion detection services/intrusion
prevention services)
Unified threat management
Identity and access management
Vulnerability scanning
MSS 1.0 may also incorporate advanced services such as DDoS, managed SIEM, and managed
SOC. MSS 2.0 spans both basic and advanced MSS, as well as professional/complementary
services (for more details, see Market Definition). MSS 2.0 providers also invest in mobile/IoT,
cloud, threat intelligence/Big Data analytics, incident response/forensics, and advanced detection
techniques. Cloud, mobile/IoT, and Big Data are three of the four pillars that IDC has identified as
top trends. The fourth pillar, social media, does not factor into this IDC MarketScape. However,
advanced MSSP capabilities can help detect, analyze, and protect against security threats in the
social media arena.
Security, in general, is complicated by the shortage of security talent. Innovative MSSPs focus on
short- and long-term employee acquisition, training, and retention using both traditional and
progressive practices. Some of their tactics are apprentice programs, scholarships, in-house
universities, university partnerships, and flexible career paths.
Further, regulatory requirements continue to evolve, and MSSPs can provide the expertise and
evidence needed for oversight and compliance based on industry-standard certifications.
Businesses are increasingly turning to MSSPs to monitor and manage some or all their security
needs. Based on IDC's market sizing and forecasting, the MSS market is expected to continue to
see growth well in excess of generic outsourcing in the coming years. MSS 3.0 trends to focus
heavily on MDR features and functions.
LEARN MORE
Related Research
EMEA Security Appliances Market Directions, 3Q21 (IDC #EUR148557121, December
2021)
©2022 IDC #EUR146178820e 12 Central and Eastern Europe Security Solutions Forecast, 2021-2025 (IDC
#EUR147312421, December 2021)
Splunk Strengthens its European Security Market Position (IDC #EUR148376921,
November 2021)
IDC FutureScape: Worldwide Future of Trust 2022 Predictions (IDC #US47193621,
October 2021)
Bringing a Zero-Trust Architecture to Secure IoT (IDC #EUR148235621, September 2021)
IDC European Security Survey 2021: Stakes Are High (IDC #EUR248207621, September
2021)
Cybersecurity in IT/OT Convergence Initiatives (IDC #EUR148045221, July 2021)
BT Partners with SAFE, Building Capabilities in Risk Quantification and Breach Predictions
(IDC #EUR248207621, July 2021)
European Security-as-a-Service Forecast, 2020-2024: Supporting the "New Normal" (IDC
#EUR246940620, January 2021)
Synopsis
This IDC MarketScape analyzes 14 managed security services providers (MSSPs) in Europe. It
examines the quantitative and qualitative characteristics of each vendor, accounting for the
prevailing trends that customers need and expect to see from their MSSPs. It is based on a
comprehensive and rigorous framework that examines how vendors compare with one another. It
also considers the key factors that are expected to be most strategic in determining vendors' ability
to meet the evolving needs of MSS customers over the short and long term.
This IDC MarketScape has identified eight Leaders in the European MSS market: Accenture, Atos,
BT, Capgemini, IBM, Orange, Telefónica, and Verizon. It has also identified six Major Players:
Deloitte, DXC Technology, Fujitsu, Deutsche Telekom's T-Systems, Wipro, and HCL.
"Adopting cloud services and remote work practices has added new layers of complexity for IT
security practitioners to address," said Joel Stradling, research director, IDC European Security
and Privacy. "This combination, in addition to the growing sophistication of the cyberthreats
companies face, is driving strong demand for MSS in Europe."
"Successful MSS providers need to provide flexibility in their MSS contracts. Businesses tend to
make decisions based on providers' demonstrations of technical flexibility to meet their unique
requirements. Customers are also looking for partners that clearly understand where the prospect
is on the evolutionary path toward secure IT infrastructure and managed services," said Claudio
Stahnke, senior research analyst, IDC European Security and Privacy.
©2022 IDC #EUR146178820e 13About IDC International Data Corporation (IDC) is the premier global provider of market intelligence, advisory services, and events for the information technology, telecommunications and consumer technology markets. IDC helps IT professionals, business executives, and the investment community make fact-based decisions on technology purchases and business strategy. More than 1,100 IDC analysts provide global, regional, and local expertise on technology and industry opportunities and trends in over 110 countries worldwide. For 50 years, IDC has provided strategic insights to help our clients achieve their key business objectives. IDC is a subsidiary of IDG, the world's leading technology media, research, and events company. IDC U.K. IDC UK 5th Floor, Ealing Cross, 85 Uxbridge Road London W5 5TH, United Kingdom 44.208.987.7100 Twitter: @IDC blogs.idc.com www.idc.com Copyright and Trademark Notice This IDC research document was published as part of an IDC continuous intelligence service, providing written research, analyst interactions, telebriefings, and conferences. Visit www.idc.com to learn more about IDC subscription and consulting services. To view a list of IDC offices worldwide, visit www.idc.com/offices. Please contact the IDC Hotline at 800.343.4952, ext. 7988 (or +1.508.988.7988) or sales@idc.com for information on applying the price of this document toward the purchase of an IDC service or for information on additional copies or web rights. IDC and IDC MarketScape are trademarks of International Data Group, Inc. Copyright 2022 IDC. Reproduction is forbidden unless authorized. All rights reserved.
You can also read